The world spends billions of dollars on cybersecurity protection technology and services each year, yet one of the most effective attacks on an organisation is a simple phishing email. These phishing emails are frequently the precursor to ransomware attacks, as many organisations around the world have discovered.
So how did we managed to turn email, an essential part of any business environment and a core part of our personal lives, into the most commonly used internet attack precursor mechanism.
The internet, as we know it, was born in November 1977 when the first internetwork connection was made.
This fledgling internetwork primarily used the US Defence Department Arpanet network, and because the underlying infrastructure was secure, little consideration was made with regard to security of the transmission protocols. This lack of inherent security continued into Internet Protocol version 4, that’s the version that most of the world uses today, when it was released in 1981.
In 1982, the specification for the simple mail transport protocol, or SMTP, was released, again, without any security specification.
Some changes were made to the protocol in 2008, but fundamentally this basic SMTP protocol is still the means by which the worlds email systems exchange information.
It is now possible to secure the transmission of email across the internet using encryption, but this only prevents the interception of information in transit and it does not fix a fundamental flaw that has been there since SMTP’s inception.
The flaw lies within the From field. This flaw makes it possible to easily change the content of the From field to anything the sender likes, and the underlying transport system will still deliver the message. This first led to the rise of SPAM, and then later on to the massive growth in phishing attacks. These spammers and phishing attackers simply change the From field to make it look like the email is coming from a valid source and then send the email out.
We are now in a situation, in 2018, where our email communications are using a thirty five year old insecure email protocol, together with an thirty six year old insecure transmission protocol over an inherently insecure network.
So why didn’t we just fix SMTP?
The challenge here is that the world is so dependent upon the core SMTP protocol that we can’t simply switch to a new email system. All we can do is append controls to help resolve the inherent vulnerabilities.
Over the years a number of things have been done to help the situation.
Sender Policy Framework was the first step.
Now eleven years old, SPF is a simple system that allows email receivers to check that incoming email is being received from a mail server authorised to send email on behalf of a specific domain.
Domain Keys Identified Mail, DKIM, takes this one step further by adding an encrypted key to outbound mail which the email receiver can validate against a public key held within the organisations’ public DNS records.
The real breakthrough comes with DMARC, which uses SPF and DKIM, and adds specific instructions to email receivers as to how to handle email that doesn’t pass the SPF and DKIM checks. DMARC is now the subject of a worldwide awareness campaign being run by the Global Cyber Alliance as part of its mission to reduce systemic cybersecurity risk.
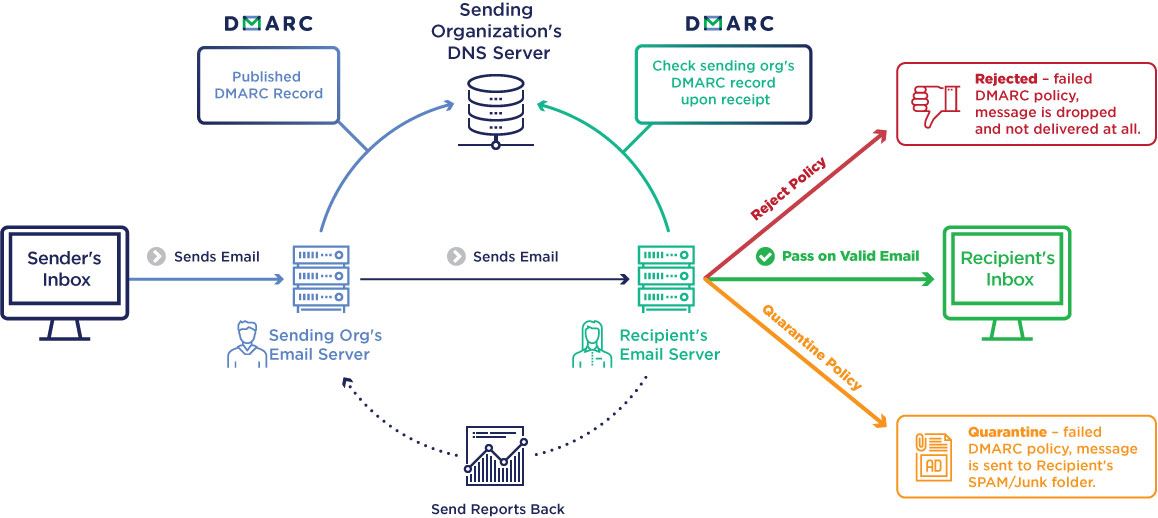
DMARC stands for Domain-based Message Authentication, Reporting and Conformance. It’s like an identity check for an organisation’s domain name. A DMARC policy allows a sender to indicate that their messages are protected, and tells a receiver what to do if one of the authentication methods passes or fails – either deliver the message, or reject the message.
With over 85% of consumer email accounts in the United States, and 70% across the globe capable of being protected by DMARC, it is now the turn of business, government and any other organisation sending email under their own domain name to do their part.
The United Kingdom and United States Governments have mandated that DMARC be implemented on all government email domains. The UK Government is already seeing the benefit of implementing DMARC with hundreds of thousands of falsified .gov.uk emails being prevented from being delivered to unsuspecting recipients.
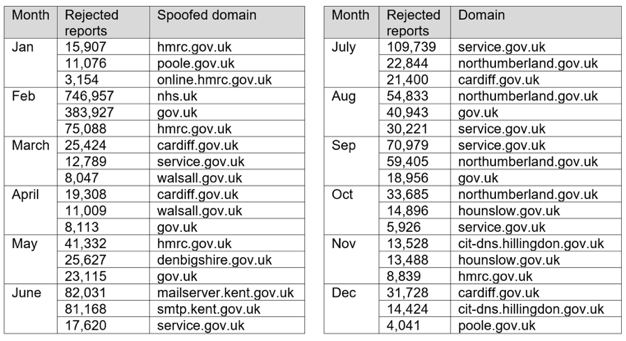
source: UK National Cyber Security Centre, February 2018
Now is the time for all New Zealand Government departments, local authorities and businesses with their own email domains to implement DMARC. It protects email reputation, improves deliverability, and helps reduce the incidence of phishing.
It is easy to start on the DMARC path and the Global Cyber Alliance provides free tools and training materials to help you along the way. Visit dmarc.globalcyberalliance.org for more information.
Author
Tony Krzyzewski FIITP is one of New Zealand’s best known cybersecurity specialists. SAM for Compliance Ltd, run by Tony and his wife Jackie, became the first Australasian member of the Global Cyber Alliance in 2017. Tony is an active participant in Global Cyber Alliance awareness programmes and was one of six cybersecurity specialists presenting at the Global Cyber Alliance / Verizon ‘Cyber Trends 2018’ event hosted by the Lord Mayor of London at Mansion House in April.


